On 25 February 2019 security consultant Bob Diachenko discovered an enormous database of emails and other personal information. The database was not password-protected and available to anyone with an internet connection.
Diachenko worked quickly to figure out the extent of this data breach and found that it contained 763 million records. According to his blog, it is 'perhaps the biggest and most comprehensive email database [he has] ever discovered'. Troy Hunt of HaveIBeenPwned estimates that it is the second biggest data breach in history.
Mar 08, 2019 Verifications.io is a company that approves or verifies email addresses for third parties. They ensure that third-party email marketing campaigns are delivered to verified email accounts instead of fake ones. Here’s the potential damage: 763 million unique email addresses. Mar 10, 2019 Although the databases were accessible for some time, as soon as the problem was disclosed to Verifications IO the service was taken offline and remains so. Which means that bad guys alerted. Security professionals discovered the data breach which involved one of Verifications.io’s online databases that had almost no security protections at all. After the leak was discovered, Verifications.io shut down the service’s official website and has been refraining from commenting on the situation ever since. Data cleansing is a process used in marketing to maintain proper email list hygiene. There are many companies out there, all with different levels and quality of service, but we’ll go over a few methods we use at Verifications.io.
You would imagine that a database that size must be an accumulation of several previous data breaches, right? Wrong. All the evidence pointed to a single source. Verifications.io, a self-described 'big data email verification platform.'
On their now archived website, Verifications.io claims to help companies 'enhance their email list', 'remove hard bounces' and improve return on investment. But while this all seems above board, this kind of service is also a phishing scammer's dream and has great potential to be misused. As we discussed in our last blog, scammers need verified emails to help them bypass spam filters and evade law enforcement. A service that verifies emails would be a useful shortcut for malware spammers.
Verifications Io Breach Update
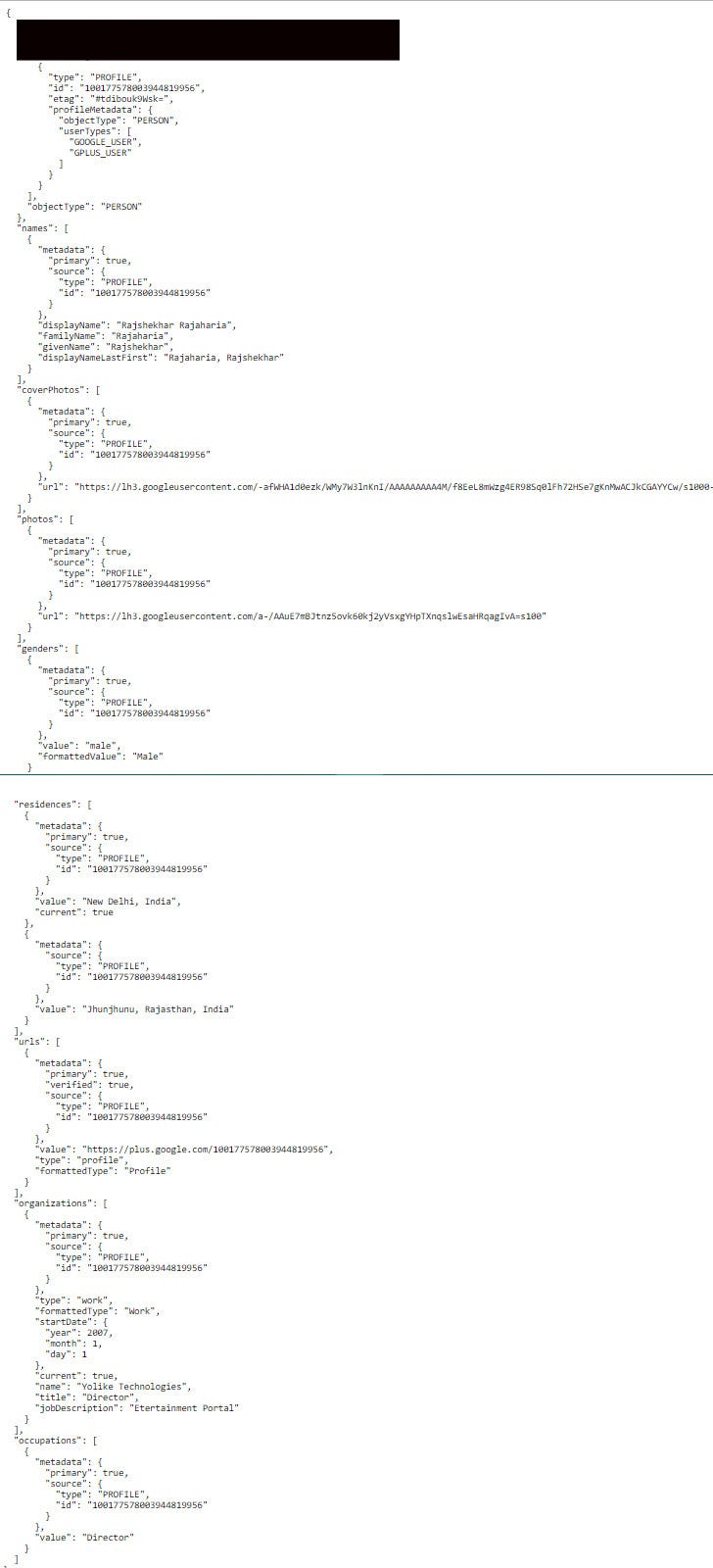
What particularly disturbed Diachenko was how detailed some of the profiles were. Data included:
- Email addresses,
- Names,
- Dates of birth,
- Employers
- Job titles,
- Genders,
- Geographic locations,
- IP addresses,
- Phone numbers,
- Physical addresses.

Verifications.io Database List
Verifications.io claimed that they drew data from publicly available sources. Does this imply that personal data online is fair game to be trawled and potentially misused?
Hunt was curious about where exactly Verifications.io mined their data. So he sent out a tweet calling on people who use unique email addresses to see which of their accounts were compromised. Though nothing has been confirmed, respondents variously claimed that their single-use email addresses for Adobe, LinkedIn and Deluxe Check Company, LinkedIn, and TechNet Magazine were implicated.
Verifications.io Database Examples
Now is a good time to reflect on how much of your data there could be out there. Every online subscription, eCommerce store, or online service you have ever signed up for has the potential to be mined. Within your company, which highly visible people could be targeted by hackers and malware spammers? It should be of great concern that Verifications.io can operate above board despite selling our sensitive data to be used far beyond the context in which the data was obtained. It is, of course, even more worrying that the data breach exposed this information to the general public.
Oracle Database Io Size
This is the new reality of life online, and it won't change any time soon. The onus is on us to actively protect ourselves, and that starts by understanding what a hacker would see if they came looking at your company.